“Beware the unseen enemy that takes not your possessions, but your very ability to act.” – Sun Tzu
“Beware the unseen enemy that takes not your possessions, but your very ability to act.” – Sun Tzu
This week, the markets are absorbing the fallout from a new and profound disruption in the global supply chain. A ransomware attack, confirmed by the European Union Agency for Cybersecurity (ENISA), targeted a key provider of airport technology, Collins Aerospace, bringing check-in systems at major European hubs like London’s Heathrow, Brussels, and Berlin to a near standstill. The chaos was immediate: manual, paper-based check-ins created lines miles long, and tens of thousands of passengers were stranded. In just the first 48 hours, Brussels Airport alone was forced to cancel or delay nearly 100 flights, while over 600 flights were affected at Heathrow.
To truly grasp the significance of this attack, we must look back. Just over a year ago, in June 2024, the BlackSuit ransomware group brought the North American Auto Industry to its knees by targeting CDK Global, the software provider for over 15,000 car dealerships. That incident, which lasted for nearly two weeks and caused an estimated $1Bn in collective losses for the dealerships, was a wake-up call for the interconnectedness of commerce. Like now, the attack was not on the individual dealership, but on the single, shared nervous system that connected them all – a well-known flaw in Monopolistic Capitalism that we seem to have forgotten to regulate these days…
The time between these two attacks has NOT been a period of calm. We’ve seen an unrelenting barrage of sophisticated cyber incidents, each a dress rehearsal for the next, larger-scale disruption. Notable among them was a significant breach of Microsoft’s SharePoint servers earlier this year, which, while not as visible to the public, was a major blow to Corporate Security. It’s a clear pattern: attackers are no longer content with a single prize. They seek to compromise the single point of failure that allows them to hold entire industries for ransom.

The European airport attack is not an isolated event; it is the natural and predictable progression of a strategy that was perfected on the auto industry. The fundamental flaw is our over-reliance on a few, centralized technology vendors – a single digital ‘Achilles’ heel‘ in an otherwise fortified system. This is no longer a matter of “if” a company will be attacked, but “when” their most critical vendor will be.
For investors, the key insight is that this trend makes the Cybersecurity Sector a veritable fortress of defensive growth – something we discussed with our Members earlier this month – prior to the recent attack. In fact Cisco (CSCO) was our Top Trade Alert on Sept 10th and last week we discussed the trade ideas we are now going to circle back to.
Cybersecurity is no longer a discretionary expense; it is a mandatory tax on the digital economy. The question is not whether to invest, but where. As our prior sessions have highlighted, wise investors will seek the bedrock of value and proven performance in firms like Cisco, Akamai Technologies (AKAM), and Qualys (QLYS) – while exercising extreme caution with the high-flying, “bubble plays” that a single market downturn could send plummeting (CRWD comes to mind).
The market’s knee-jerk reaction to a cyberattack often benefits the most visible, high-growth “bubble plays,” but a more enduring and strategic approach focuses on the companies providing the fundamental infrastructure and resilience. These are the defensive growth champions that will benefit from the long-term, mandatory spending on cybersecurity.
Cisco Systems (CSCO): The Master of the Network
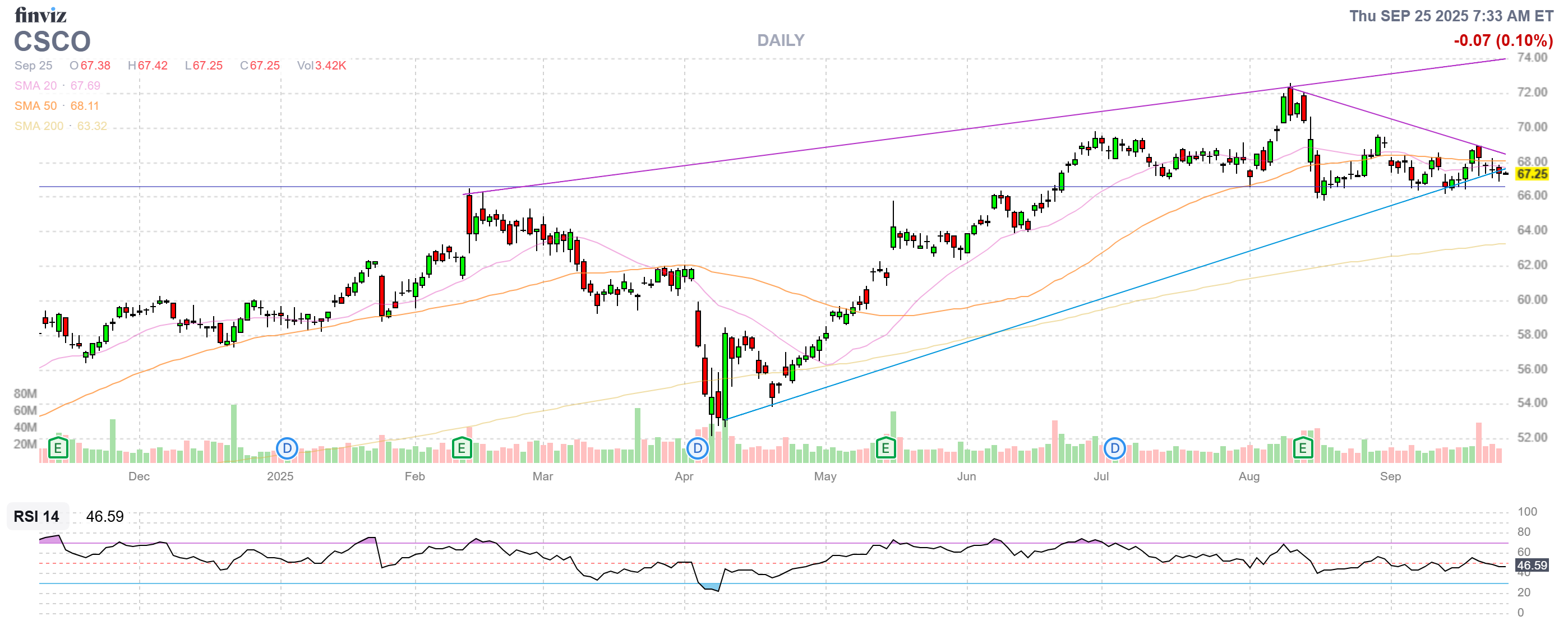
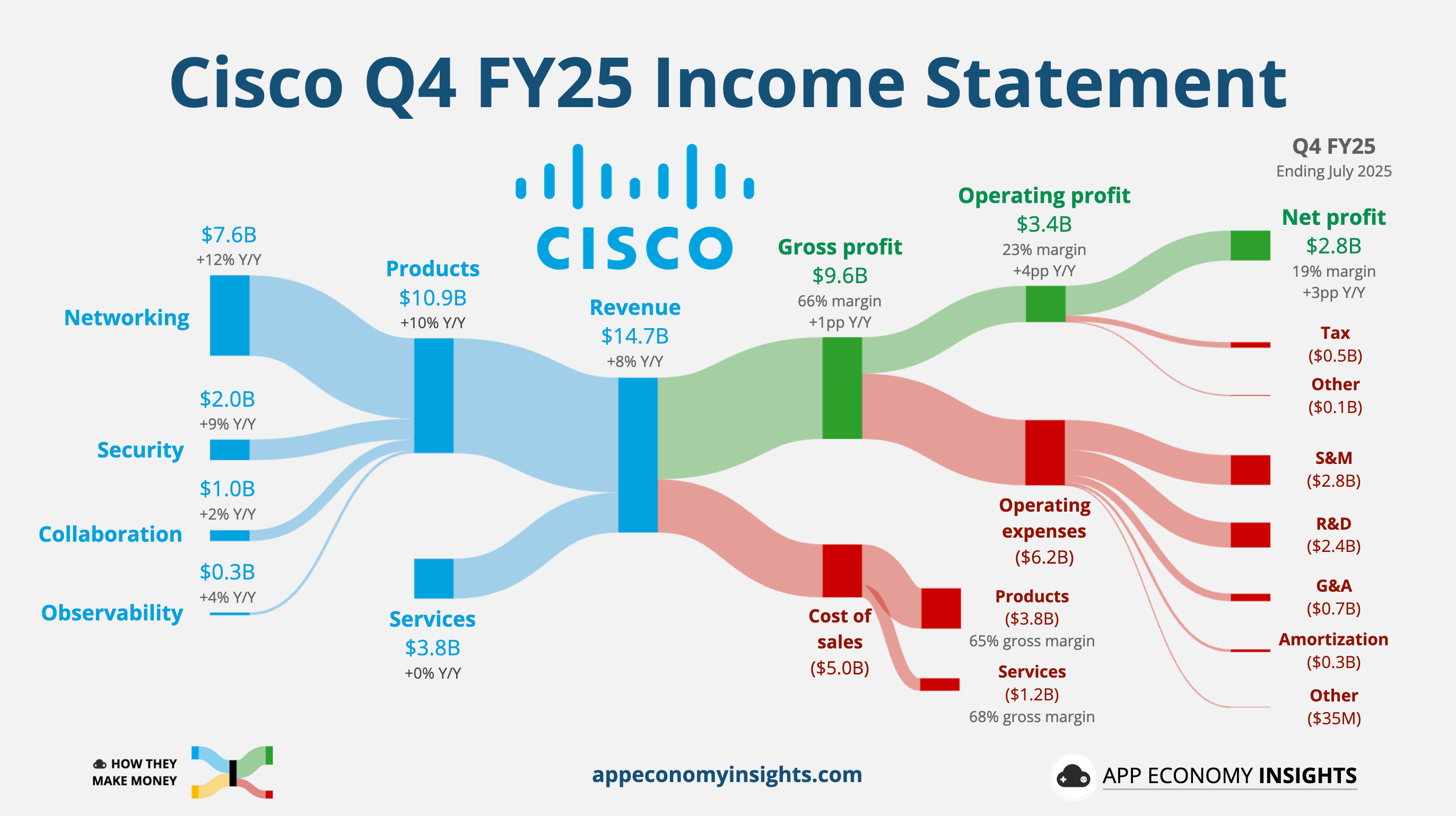
As a core position in our strategy, Cisco’s value proposition is its unparalleled command of network infrastructure. While known for hardware, Cisco’s cybersecurity arm is a full-stack force. The recent acquisition of Splunk is a masterstroke, transforming Cisco into a single-source provider for networking, security, and observability. This is crucial for industries like financial services, healthcare, and manufacturing that need a unified view of their entire digital footprint.
What Cisco does is connect the pieces – its threat intelligence from Cisco Talos integrates with Splunk’s data analytics to move from simple threat detection to a proactive stance of threat PREDICTION. The company’s investments in AI and its presence in the AI Infrastructure buildout make it a value play with significant forward-looking growth, as it’s positioned to both power and protect the AI revolution.
Akamai Technologies (AKAM): The Sentinel at the Digital Edge
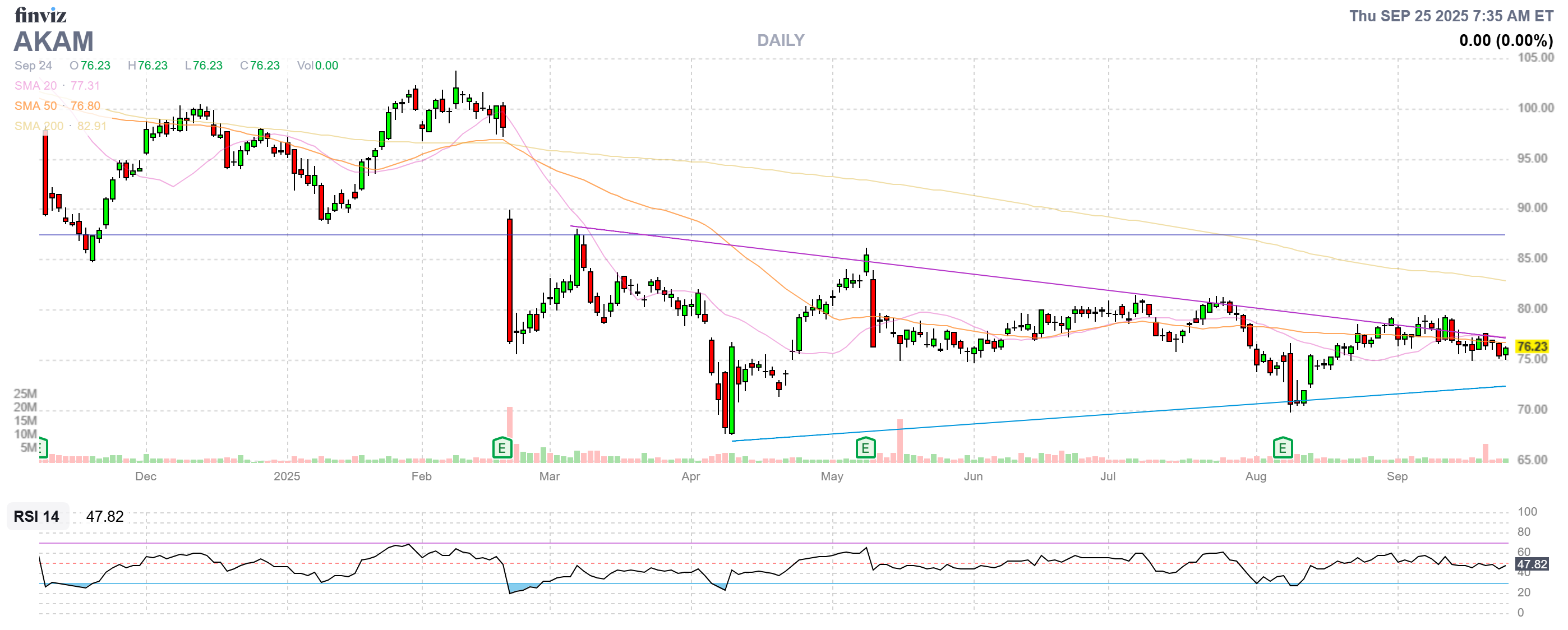
Akamai, a defensive growth play, is perfectly positioned to capitalize on the supply chain vulnerabilities we’ve been discussing. Its core strength lies in its globally distributed network, which allows it to secure and deliver content at the edge (closer to the user). This makes it a crucial partner for Ecommerce, Media, and Enterprise clients. Its security portfolio, including Web Application and API Protection (WAAP) and its Guardicore segmentation solutions, directly addresses the issue of third-party risk by allowing companies to segment their networks and prevent an attack on one vendor from crippling the entire operation.
With its security and cloud computing segments now accounting for the majority of its revenue, Akamai is a well-priced, cash-flow-generating stock that offers a direct and tangible solution to the problem of a fragmented attack surface.
Qualys (QLYS): The Surveyor of the Digital Fortress
Qualys is a tactical position and a contrarian play, operating on the principle that you cannot defend what you cannot see. Its core business is vulnerability management, providing a cloud-based platform that gives companies a continuous, real-time view of their IT assets. Qualys automatically scans for weaknesses, from unpatched software to outdated apps, and prioritizes remediation efforts based on risk.
This is not a “firefighter” solution; it’s a “castle inspector.” Its value lies in its mandated nature – businesses across all industries, from retail to government, require continuous compliance and vulnerability assessments to meet regulatory requirements. Qualys’s reasonable valuation (20x forward earnings) and its foundational role in any security program make it a compelling investment for those who believe that mandatory, recession-resistant spending on cybersecurity will continue to rise.
Key Takeaways for Investors:
-
The Unrelenting Threat: The cadence of major attacks on shared infrastructure is escalating, with a clear financial and operational cost.
-
The Power of the Supply Chain: The attacks on CDK Global and Collins Aerospace demonstrate that the greatest vulnerability lies in third-party vendors.
-
A Pivot to Value: In a market driven by mandatory spending, finding cybersecurity stocks with reasonable valuations and a proven track record is the most prudent strategy.
We will provide some actionable plays in our Live Member Chat Room (join us HERE) and keep on top of this topic as the situation develops. We also need to consider which of our investments are particularly vulnerable to attacks as the downside of AI and Quantum Computing is it makes it possible to design attack systems that are capable of slicing through existing security.
This is a race that will be running for years to come.